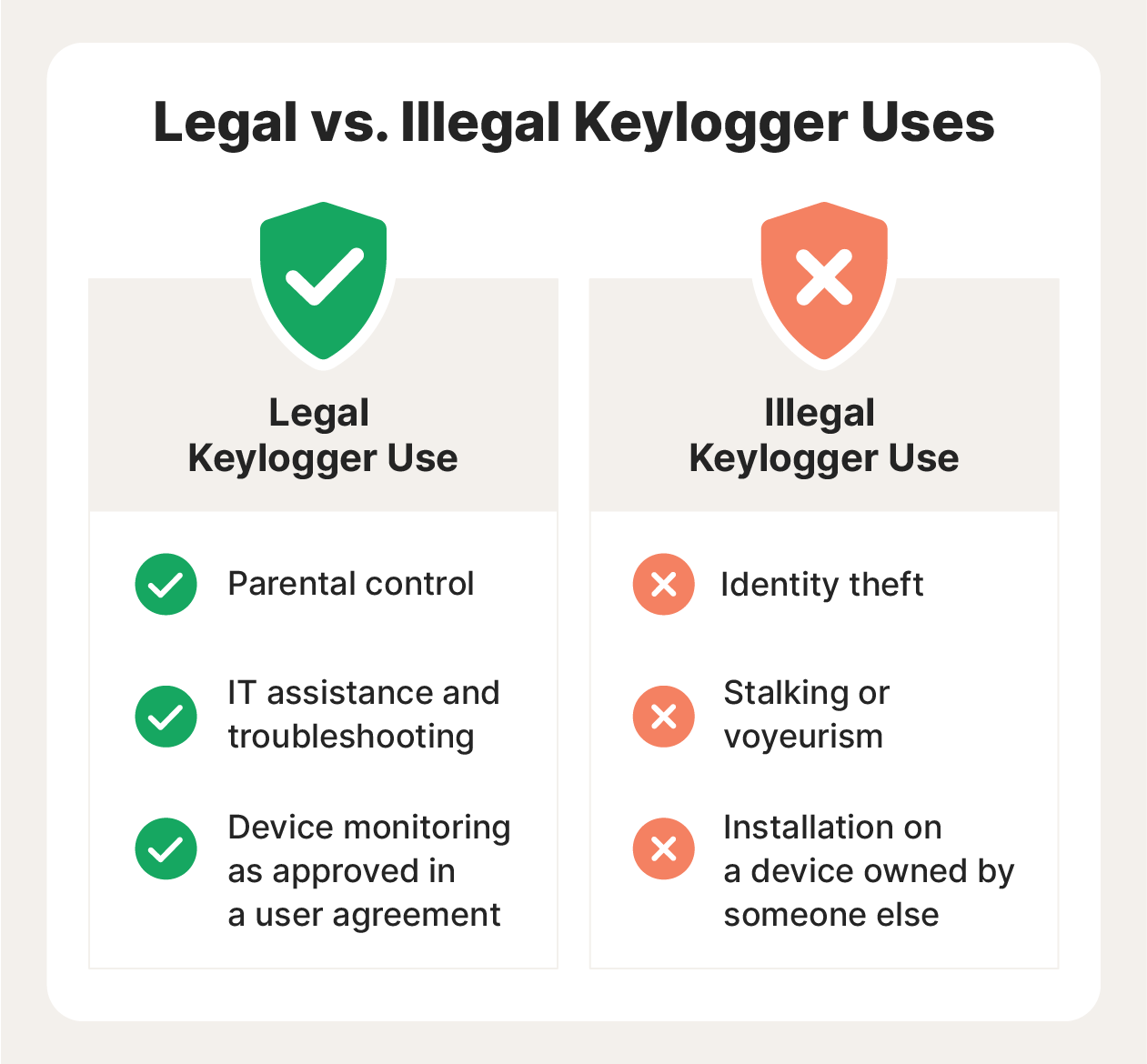
Looking Good Tips About How To Detect Keystroke Logger
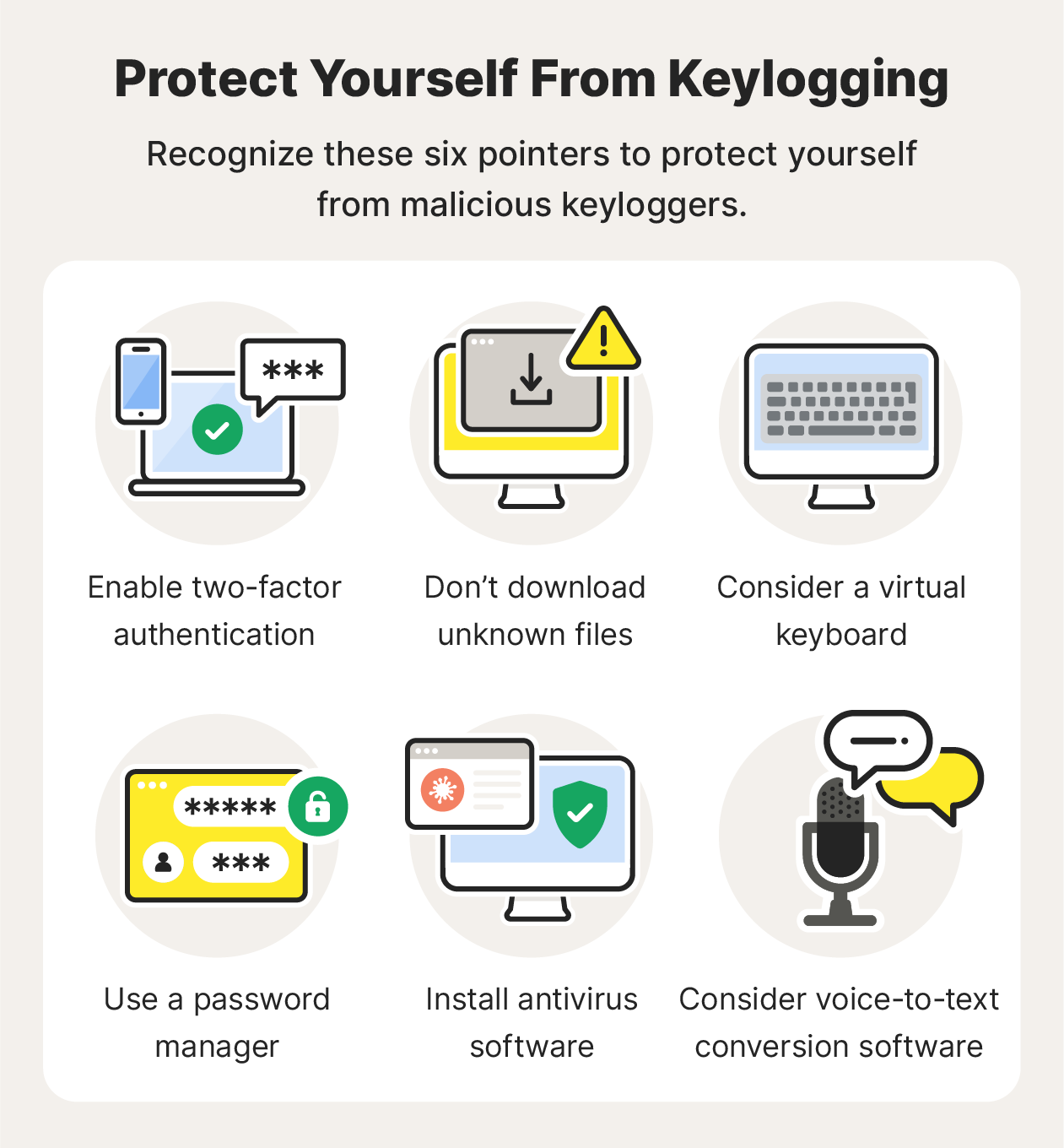
Though it is difficult to detect and remove keystroke loggers for they adopting various technologies, it is still possible to remove certain types of keyloggers.
How to detect keystroke logger. Keylogger tools can either be hardware or software meant to automate the process of keystroke logging. However, keyloggers can also enable cybercriminals to. 6 answers sorted by:
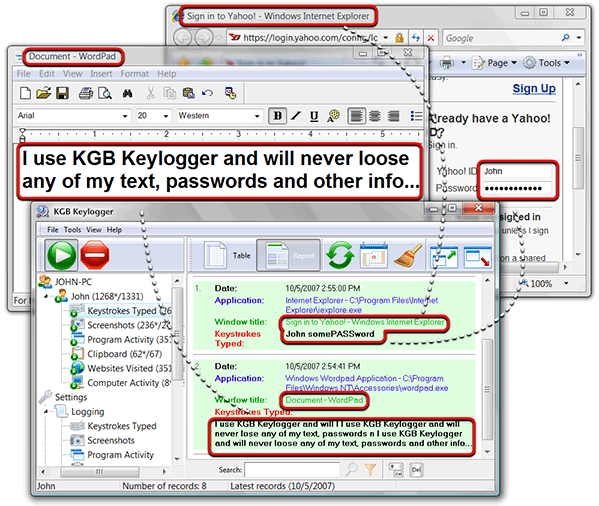
In a keylogger attack, the keylogger software records every keystroke on the victim’s device and sends it to the attacker. These tools record the data sent by every. Keystroke logging is a real threat that you need to be aware of if you want to protect your privacy and security.
At the top right corner of the browser, click on the three dots (the burger menu). Currently, keystroke research is in its. A keylogger, sometimes called a keystroke logger, is a type of surveillance technology used to monitor and record each keystroke on a specific device, such as a computer or.
On the left side of the window, find the reset option (can be. A keylogger, also known as a keystroke logger, is a type of spyware that can be installed on a computer, phone, or tablet to monitor and record keystrokes and touches. Keystroke logging focuses on the process or writing, not the product.
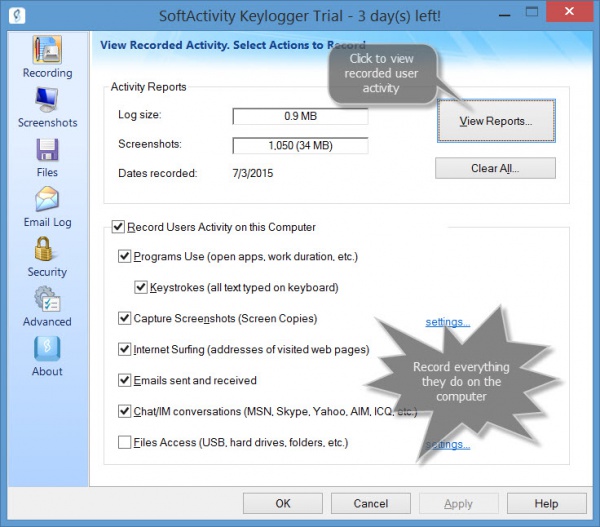
The software is installed on your computer, and. You may notice that your computer is unusually slow or unstable. A keylogger, short for keystroke logger, is a type of surveillance software or hardware that records every keystroke made on a specific computer or network without.
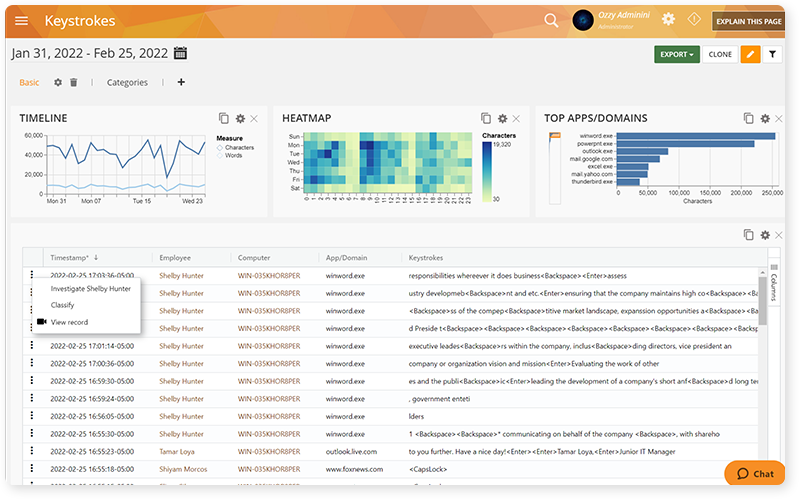
9 following the change of emphasis of the title of the question to how do i detect keystroke loggers in a reliable way? much of my answer. Here’s how you can detect keyloggers on your computer: Some keylogging software can also record mouse movements, screen images, clicked website links, and other user input actions.
Here are the most common ones: This is usually a sign of malicious software running in the. Software that logs what you type on your keyboard.
Enter keystroke logging and its potential applications.